Ukraine’s IT Army now aids drone strikes on Russian oil refineries
Once focused on disrupting Russian banks and businesses, Ukraine's volunteer hacker group is now shifting to Russian military targets, from Starlinks to CCTV cameras during long-range drone raids


As the world continues to become more digitized and reliant on the Internet, “the opportunity for cyber-attacks will only grow,” said one of the lead coordinators and the spokesperson of the IT Army of Ukraine, who goes by the callsign Ted.
In an exclusive interview with Euromaidan Press, Ted discussed the organization’s evolution, emphasizing the need for non-technical solutions to reach and recruit the average person, thus scaling the IT Army’s impact on Ukraine’s war effort.
Ever since Ukraine’s government issued a digital call to arms at the start of Russia’s full-scale invasion, the IT Army of Ukraine met the call by organizing a decentralized volunteer hacker army to fight Russia in cyberspace. The operations of the IT Army continue to grow more efficient in support of Ukraine’s battlefield objectives.
Over two years since the start of Russia’s full-scale invasion, the IT Army is not only enacting what Ted believes is an additional form of economic sanctions through cyber-attacks but also disrupting Russia’s battlefield operations. Ted believes that with more resources and people, the IT Army “could do way more.”
Once the Russian army opened a new front in Kharkiv in May, the Ukrainian IT Army posted on their Telegram channel in response: “We are currently working on important targets related to events at our border in the Kharkiv Oblast. We are trying to disrupt the enemy’s communications. We need more power! Activate everything!”
Democratizing cyber-warfare
“DDoS attacks are a very simple way to interfere with Russian operations,” said Ted, “the IT Army has developed a unique expertise in conducting DDoS attacks, and Russia is very vulnerable to these attacks.”
The attacks conducted by Ukraine’s IT Army are simple in nature: Distributed Denial of Service (DDoS) attacks. If you gather enough computing power from different computers, hackers can form a botnet capable of overwhelming and taking down entire networks.

Pascal Geenens, the Director for Threat Intelligence at cybersecurity firm Radware, which helps provide protection against DDoS attacks, wrote that “The IT Army of Ukraine’s innovative approach to engaging the public in cyber warfare has significantly contributed to the democratization of DDoS attacks.”
The website of the IT Army provides detailed resources that lower the barrier to entry for anyone wanting to engage in cyber war on Ukraine’s behalf. There are detailed guides on how to install the “IT Army Kit,” which contains the tools needed for conducting DDoS attacks.
Volunteers can even use the toolkit to schedule resource utilization on their computers so that their attacks run in the background, minimizing interference with daily activities. Leaderboard statistics are also posted on the Telegram channel to help gamify the process, thereby promoting competition and increasing engagement among participants.
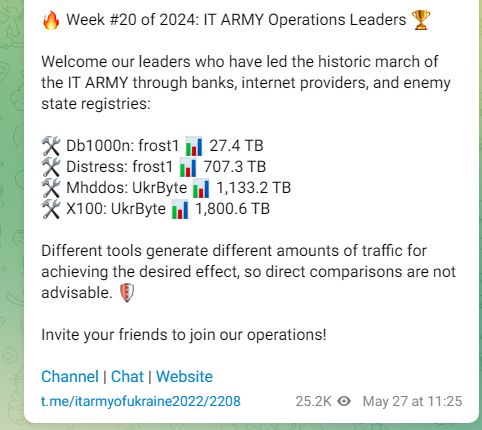
The IT Army provides participants with a list of targets. Ted said that to address risk, “our tools are designed in such a way that the user can only pull a list of targets from our repository that we control.”
Gazeta.Ru reported in April 2024 that almost half of the companies in the top 100 by revenue in Russia do not have “professional protection” against Layer 7 DDoS attacks. Layer 7 attacks specifically target the application layer of the network and can cause severe disruptions by overwhelming web servers and applications.
“If a Russian company wants to be protected against DDoS attacks, they must buy expensive software such as Cloudflare. It costs a lot of money, and if the company has a lot of infrastructure, it can cost them hundreds of thousands of dollars to protect. Not everyone wants to spend money on this,” Ted remarked.
The evolution of cyber targets
Throughout the war, the IT Army attacked Russian banks, businesses, and infrastructure. But over time, the group realized its cyber offensive could grow to play a more critical role on the battlefield.
By October 2023, the IT Army conducted an offensive to disable internet services in Russian-occupied parts of Ukraine.
“Internet providers have become our sweet spot as it’s hard for them to build protection against us,” Ted stated.
Attacks on internet providers cause maximum collateral damage. Not only does internet service get disrupted for businesses, maximizing economic losses; Ted believes it disrupts the Russian war machine, too.
“War is extremely digital now. The enemy uses civilian telecommunications for military purposes near the frontline,” Ted said. “They are a priority target for us.”
He pointed out the recent case of the Russian military using Starlink on the battlefield. If the IT Army is able to disrupt communications near the Russian administrative points, they won’t be able to see their drone feed data from the front.
The IT Army’s campaign against Russian Internet providers once led to a disruption of 40% of their resources, causing widespread disruption in service. The Russian news website Kommersant wrote, “The number of DDoS attacks on Russian companies doubled year on year in the first quarter. Mostly companies from critical industries…Roskomnadzor speaks of repelling almost three times more attacks in the first quarter alone than in the entire 2023.”
In one attack on the federal internet provider JustLan, the IT Army noted that they “might as well be renamed to JustDead. It would sound cooler and match the current state.”
On 28 April 2024, the IT Army posted on their Telegram: “For five days, we kept the provider Ufanet offline. It’s not because they can’t do their job; it’s because with each operation, we get better—better intelligence, better software, more of you joining with your capabilities.”
In the same month, the hacker group also concentrated an attack against two of the largest satellite internet providers, Astra and Allegrosky, which were down for a few days in a row. Russian media reported in May 2024 that the number of DDoS attacks on the Russian energy industry had increased tenfold over the past year.
Scaling a hacker army
Ukraine’s volunteer IT Army wants to continue scaling their impact, which requires broader participation. To increase the rate of engagement, The IT army turned to marketing agencies.
“Once we started to speak with them, the marketing agencies brought a few ideas, and it was cumbersome,” Ted said.
The marketing team suggested ideas like a complete overhaul, creating a short movie, rebranding the IT Army to demystify the hacking component, and updating the website. Ted simply wanted quick changes. To fund these marketing improvements, funding would need to be crowdsourced, and collecting money creates problems of its own.
If the group tries to make content to post on social networks to promote people joining a hacker army, those networks remove the IT Army’s posts. Ted points out. Even social influencers attempting to help also face content blocks.
“Many people consider us operating in a grey area,” said Ted. While the Ministry of Digital Transformation helped put out the initial call for people to join the IT Army at the start of the war, it doesn’t actively promote the group anymore.
“We have no direct communication line to the Ministry of Digital Transformation. We only engage with their PR team occasionally,” noted Ted. With better support and engagement, the IT Army could have an easier time getting more people to join, but it seems to be a lower priority for Ukraine’s government.
Previous legislation integrated the IT Army into the Ministry of Defense of Ukraine, but the efforts appear to have fizzled out. Speaking about the progress of the legislation, Ted said, “Maybe it’s undervalued, and lawmakers don’t see it as a high priority.”
However, whenever the IT Army does get to speak with government officials to get feedback, Ted points out that they are “happy and never expected it to be such a good thing.”
Russia feels the impact
For the Kremlin elite, Ukraine’s volunteer hacker army is not just an obscure cyber group operating in the background.
Oleg Syromolotov, then Deputy Minister of Foreign Affairs of the Russian Federation, claimed in December 2022, “The USA plans to spend more than $11 billion next year on cyberattacks against undesirable governments. In the so-called ‘Ukrainian IT army,’ we are dealing not with homegrown hackers but with the full cyber power of the North Atlantic alliance, which is making relentless efforts to test Russia’s resilience ‘under the flag’ of pro-Ukrainian hacker groups.”
Help us make more articles like these — become a patron.
Similarly, in March 2024, Dmitry Gribkov, an aide to the Russian Security Council, warned Western officials that supporting the IT Army was akin to opening Pandora’s box, which would ultimately backfire against its “masters.”
Gribkov claimed that “Hacking experts are being trained in Ukraine and the Baltic states to carry out computer attacks on Russia’s information infrastructure.” He further emphasized that Ukrainian officials are openly involved in “mass cyberattacks on Russian information infrastructure facilities.”
“If it was not so painful, the Russian security council wouldn’t be issuing statements on the IT Army,” said Ted.
Supporting the physical battlefield with the digital
While the war on the battlefield rages on, both sides continue to seek out opportunities to gain the upper hand. Ukraine’s hacker army is determined to help the Armed Forces of Ukraine prevail in battle. Ted, with a slight grin, noted that Ukrainian intelligence services reached out to him around the time Ukrainian drones began hitting Russian oil refineries. “We were asked at that time to help turn off CCTV in parts of Russia,” noted Ted.
As a result of this request, the IT Army of Ukraine began conducting cyber-attacks against Russian internet providers to disrupt video feeds around areas where Ukrainian drones were attacking. This disruption aimed to hinder Russia’s visibility of the drones and ensure mission success.
Ted is optimistic that the Ukrainian hacker army did end up playing an important role in supporting Ukrainian drone attacks in Russia. “We are just beginning to have a significant impact on Russia’s military,” said Ted.
Related:
- DW: How Ukraine’s hackers attack Russian targets on cyber front lines
- How Ukraine built a volunteer hacker army from scratch
- Ukraine’s IT Army disrupts key Russian online services



